IDD Bureau
A federal grand jury of the United States has indicted two Chinese nationals for hacking computer networks of companies, including defence contractors, solar energy companies even those developing COVID-19 vaccines, to data.
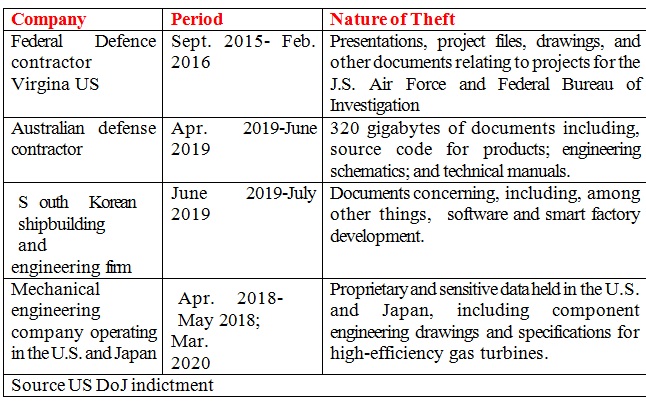
At least three of military-equipment companies impacted– are in Japan, Australia and South Korea, the Asia-Pacific region — where China is trying to expand. Other companies are in the US and in European Union.
Among other data stolen through the hack across globe, are key engineering drawings and specifications for high-efficiency gas turbines of a company working for the US and Japan . Besides this shop floor designs of a South Korean Ship maker have been stolen while another Australian contractor has been compromised for an un-specified product. Also presentations, project files, drawings, and other documents relating to projects for the Air Force and Federal Bureau of Investigation, have been stolen.
The US Department of Justice (DoJ) has put out a detailed 27 page indictment order (read it here).
The Grand Jury concluded that Chinese nationals Li Xiaoyu, 34, and Dong Jiazhi, 33, were working with the Chinese Secret Service , the Ministry of State Security (MSS), and other agencies of the Chinese government to steal intellectual property over a period of more than 10 years.

The Grand Jury has concluded that stolen information included details regarding military satellite programs and military wireless networks and communication systems.
Li and Dong each face 11 charges including conspiracy to commit theft of trade secrets as well as seven counts of aggravated identity theft. The hacking campaign lasting more than ten years to the present, targeting companies in countries with high technology industries,
The Chinese hackers allegedly targeted robotics, aircraft and marine engineering, clean energy engineering, biotechnology, advanced rail technology, non-governmental organizations, human rights activists in the U.S., China and Hong Kong, as well as vaccine and testing development for the coronavirus, the Justice Department said.Read it here
How the hackers worked
The indictment that comes from the Eastern District court in Washington state – where the hack was first discovered- have accused Li and Dong of working with the Chinese secret service – Ministry of State Security – and were based out of the Guangdong province. Li and Dong were tasked to steal data through computer fraud from corporations and research institutions.
Li and Dong , former classmates at an electrical engineering college in Chengdu, China, used their technical training to hack the computer networks of a wide variety of victims, such as companies engaged in high tech manufacturing; civil, industrial, and medical device engineering; business, educational, and gaming software development; solar energy; and pharmaceuticals. More recently, they researched vulnerabilities in the networks of biotech and other firms publicly known for work on COVID-19 vaccines, treatments, and testing technology.

Their victim companies were located all across the world, including among other places the United States, Australia, Belgium, Germany, Japan, Lithuania, the Netherlands, South Korea, Spain, Sweden, and the United Kingdom.
Computer systems of hundreds of victim companies, governments, non-governmental organizations, and individual dissidents, clergy, and democratic and human rights activists in the United States and abroad, including Hong Kong and China. The defendants in some instances acted for their own personal financial gain, and in others for the benefit of the MSS or other Chinese government accompany networks.
“China has now taken its place, alongside Russia, Iran and North Korea, in that shameful club of nations that provide a safe haven for cyber criminals in exchange for those criminals being ‘on call’ to work for the benefit of the state,” Assistant Attorney General for National Security John C. Demers said. The Chinese Communist party’s desire for intellectual property “insatiable,” Demers said.
“Li and Dong, “targeted industries included, among others, high tech manufacturing; medical device, civil, and industrial engineering; business, educational, and gaming software; solar energy; pharmaceuticals; defence,”
US DoJ
According to the indictment, their alleged illegal hacking activities began in September 2009 and may have lasted through July 7 of this year, when the indictment was filed.
























Recent Comments